Cyber threats to OT systems are escalating at an alarming rate, with nearly 73% of organizations reporting an intrusion impacting either OT alone or both OT and IT systems in 2024 [1] – up from 49% last year. These systems, which manage and control critical industrial processes across sectors like energy, manufacturing, transportation, and healthcare, are increasingly interconnected with IT systems due to the rise of digital transformation and the Industrial Internet of Things. Recent research further reveals a surge in intrusions that exclusively target OT, rising from 17% to 24% year-over-year[2], underscoring the urgent need to address these critical OT vulnerabilities.
Unlike traditional IT systems, OT environments face unique challenges due to their operational requirements, legacy technologies, and the need for continuous uptime. As OT systems become more connected, addressing these vulnerabilities is crucial for ensuring both cybersecurity and the safe operation of critical infrastructure.
Challenges in Addressing OT Vulnerabilities
One of the primary challenges in securing OT systems lies in their legacy infrastructure. Many OT environments consist of devices and systems that were designed decades ago, long before cybersecurity was a concern. These legacy systems often operate on outdated software and hardware that is no longer supported by manufacturers. As a result, they are vulnerable to a range of exploits that modern systems are better equipped to resist. The use of proprietary protocols and custom-built systems in OT networks further complicates the process of implementing standardized cybersecurity measures.
Moreover, unlike the IT domain, OT systems are expected to run continuously, with minimal downtime. For industries like power generation, water treatment, and manufacturing, even brief interruptions can result in significant financial losses, operational delays, or even risks to human safety. This constraint makes it difficult to perform essential cybersecurity tasks such as patching software, upgrading systems, or installing security updates without disrupting critical operations. Balancing security and uptime is a constant challenge in OT environments, with some organizations opting to delay necessary updates to avoid the cost of downtime, further intensifying vulnerability risks.
Another major challenge stems from the lack of standardized protocols in OT systems. Unlike IT environments, OT systems may use a mix of proprietary, legacy, and vendor-specific communication protocols. This diversity makes it challenging to implement universal security solutions that can protect the entire OT network. Additionally, the lack of encryption and authentication mechanisms in some OT protocols makes them susceptible to man-in-the-middle attacks, unauthorized access, and more.
The convergence of IT and OT networks presents yet another challenge. Traditionally, OT systems were air-gapped, being physically separated from IT networks and external threats. However, the growing need for real-time data analytics, remote monitoring, and process automation has led to the integration of IT and OT environments. While this integration enables more efficient operations, it also exposes OT systems to cyber threats that are more commonly associated with IT networks, such as malware, ransomware, and phishing attacks. Threat actors can exploit weaknesses in IT systems to move laterally into OT environments, where they can disrupt operations, cause physical damage, or even compromise safety-critical systems.
Solutions to OT Vulnerabilities
To address these challenges, organizations must adopt a multi-layered approach to securing OT environments, including the following key strategies:
● Network Segmentation: By separating IT and OT networks, segmenting legacy systems that are both vulnerable and critical, and implementing firewalls, organizations can effectively reduce their attack surface and limit the potential for threats to move laterally across systems.
● Zero-Trust Architecture: In a zero-trust model, no user or device is automatically trusted, even if it is inside the network perimeter. Every interaction with the OT environment is authenticated, authorized, and encrypted, minimizing the risk of insider threats and unauthorized access, even if an attacker breaches the network.
● Patching and Vulnerability Management: Organizations should schedule patches during planned maintenance windows to minimize disruption. When immediate patching is not possible, virtual patching solutions can provide interim security by shielding vulnerable systems from known exploits without requiring full system updates.
● Monitoring and Detection Tools: Utilizing tools specifically designed for OT environments can enhance real-time visibility into ICS and IIoT devices. Solutions like intrusion detection systems and SIEM platforms allow security teams to detect anomalous activity and respond to potential incidents quickly.
● Role-Based Access Control: Implementing Role-Based Access Control and the principle of least privilege ensures that users and devices have only the minimum necessary access to perform their functions. This reduces the risk of accidental or malicious changes to OT systems. Strong authentication mechanisms, such as MFA, further enhance access control by ensuring that only authorized personnel can interact with sensitive systems.
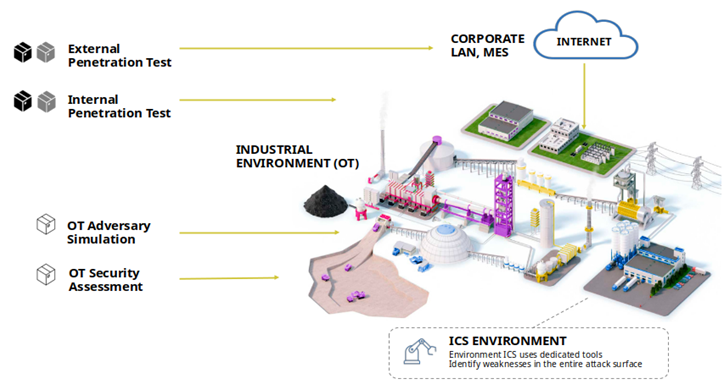
SCADAsploit: Simulating Threats in OT Networks
Given the complexities of OT environments, specialized tools are crucial for proactive vulnerability identification. HWG Sababa plays an important role in tackling these risks with SCADASploit an innovative C2 – Command & Control framework for OT developed by Omar Morando Head of Innovation Lab & OT Evangelist. Tailored specifically for SCADA and ICS systems, SCADASploit provides advanced red teaming capabilities that enable penetration testers and security teams to simulate adversarial attacks on SCADA, PLC, and IoT systems without disrupting critical operations.
By simulating various industrial protocols and components, SCADASploit equips users with valuable features such as protocol fuzzing, system emulation, and custom exploit scripting. This allows organizations to conduct realistic simulations and identify vulnerabilities unique to OT environments. As awareness of OT vulnerabilities grows – alongside the potential disruptions they pose to critical infrastructure – tools like SCADASploit are essential for helping organizations proactively identify and mitigate risks, ultimately strengthening the security of vital industrial operations.
As OT systems continue to evolve and become more interconnected, addressing their security vulnerabilities requires a multi-faceted approach. From network segmentation to leveraging advanced tools like SCADAsploit, industries can mitigate the risks posed by both known and unknown threats. With the right defences in place, OT systems can maintain the security and resilience needed to protect essential services and infrastructure.
➡️ Would you like to know more? Write to marketing@hwgsababa.com.
#WeMakeYouCyberSafe
—-
[1] 2024 State of Operational Technology and Cybersecurity, Fortinet
[2] 2024 State of Operational Technology and Cybersecurity, Fortinet