As the world moves toward greater reliance on renewable energy, Italy is setting an example. In 2024, for the first time, solar and wind power supplied 43.8% of the country’s energy demand [1], surpassing fossil fuels. However, this transition brings its own challenges, including in cybersecurity.
Italy’s Energy Infrastructure Under Threat
The Clusit 2024 report highlights a significant 65% increase in cyberattacks targeting Italy’s critical infrastructure, particularly the energy and utilities sectors. This rise far exceeds the 50% global increase noted by the World Economic Forum, underscoring the Bel Paese’s vulnerability. Its strategic location in the Mediterranean and key role in cross-border energy supply makes the country a prime target for cyber threats. Moreover, outdated legacy systems and relatively low cybersecurity budgets further expose Italy’s critical infrastructure to disruption.
Strengthening Cyber Defences
To stay ahead of the growing threats, energy and utilities companies must adopt a multi-layered cybersecurity approach, including:
● Regulatory Compliance: With the recent NIS2 Directive, it’s now essential to assess security strategies, adjust incident response plans, and ensure compliance. NIS2 is already reshaping the landscape for critical infrastructure, marking a pivotal shift in how cybersecurity is managed.
● OT Security: Outdated systems, which are prevalent in the energy sector, require specialized OT security technologies and continuous monitoring to minimize risks and protect both legacy and modern systems.
● Digital Innovation Security: As companies adopt new technologies like IoT and IIoT, they must incorporate Zero Trust Architecture and robust business continuity planning to prevent unauthorized access.
● Supply Chain Security: Threat-hunting solutions and strong digital borders are essential in defending against increasingly common supply chain attacks.
Why NIS2 Compliance is a Strategic Necessity
The NIS2 Directive, now fully transposed in Italy as of October 2024, is a game-changing regulatory framework aimed at strengthening cybersecurity across the EU. Compliance with NIS2 isn’t just a legal requirement; it’s also a strategic necessity for energy and utility companies.
Firstly, ensuring operational resilience is key to maintaining stable and secure energy production. NIS2 mandates that companies conduct cybersecurity assessments and update their incident response plans which allows them to quickly detect, respond to, and recover from cyber incidents. This, in turn, helps prevent costly disruptions and ensures public safety.
Secondly, avoiding regulatory penalties is another important aspect. Non-compliance can result in fines of up to 2% of global turnover or €10 million, posing a serious threat to an organization’s financial stability and reputation.
Building trust and gaining a competitive edge is another crucial outcome of NIS2 compliance. As customers and stakeholders place increasing importance on security, compliance can differentiate companies from competitors. A 2022 PwC survey found that 78% of consumers are less likely to use services from companies that have suffered a data breach, highlighting the value of cybersecurity in attracting and retaining customers.
Securing Critical Infrastructure from Advanced Threats
The energy and utilities sectors have become frequent targets for cyberattacks, especially from APT groups and state-sponsored actors. These attackers aim to disrupt critical infrastructure, as evidenced by high-profile incidents like the Industroyer and Industroyer2 attacks.
With nearly 70% of cyberattacks in 2023 directed at critical infrastructure [2], it’s clear that these sectors are facing persistent threats. Interestingly, 85% of these attacks could have been prevented with basic security practices[3], such as patching vulnerabilities, implementing multi-factor authentication, and adhering to least-privilege principles.
However, for sectors as vital as energy, basic protections are not enough – advanced, specialized cybersecurity measures must be employed. Consider the following approaches:
● Micro-segmentation: Dividing networks into smaller, isolated segments can significantly reduce the impact of breaches. For critical sites with a mix of old and new systems, micro-segmentation can reduce breach impacts by up to 40%.
● Dedicated OT security solutions: Technologies designed for OT networks provide visibility and advanced threat detection, preventing minor incidents from escalating.
● OT SOC: Expanding SOC to include OT data ensures ongoing monitoring and swift response to any security incidents.
Tackling IoT Vulnerabilities in Critical Infrastructure
The growing adoption of IoT and IIoT devices in critical infrastructure is introducing significant security challenges. These devices, used to monitor grid performance and manage key assets, are often vulnerable to cyberattacks due to insufficient protections. Indeed, recent research shows that over 50% of security managers believe their current technologies are inadequate for effectively protecting IoT devices [4]. In response, the New Machinery Regulation, which came into effect in April 2023, requires stronger security measures for IoT and IIoT devices in critical infrastructure settings.
Key steps to mitigate these risks include:
● Assessing and Fixing Vulnerabilities: Regular assessments of IoT devices help identify and address weaknesses, ensuring operational continuity and data protection.
● Gestione dei dispositivi non monitorati: Many IoT devices are often overlooked, making them vulnerable to attack. Implementing robust security protocols for these devices is critical.
● Monitoring DNS Traffic: Proactively scanning DNS traffic across all devices can help identify anomalies early, allowing for quick responses to potential breaches.
Supply Chain Attacks: An Escalating Threat
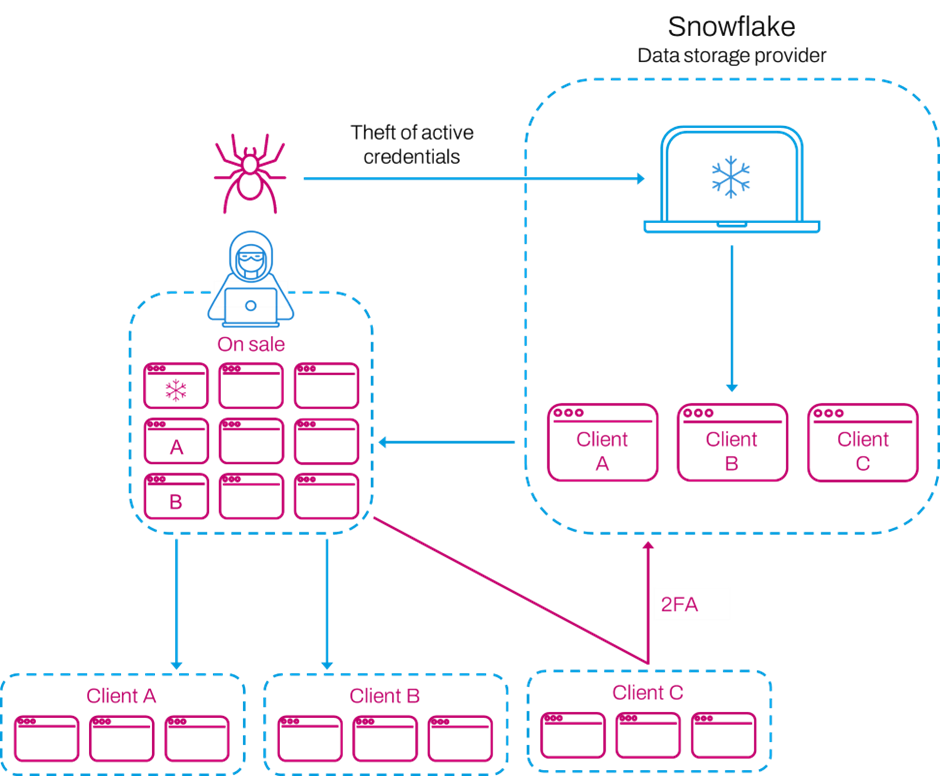
Supply chain attacks have become a major concern for critical infrastructure. These sectors rely on extensive networks of suppliers and service providers, each of which can introduce vulnerabilities. Attackers often target less secure elements, such as third-party vendors and hardware suppliers, to gain access to sensitive data. Recent examples, like the Snowflake, cyberattack, show how such attacks can impact multiple sectors at once.
To effectively mitigate the growing risks associated with supply chain vulnerabilities, companies must adopt rigorous security practices across their operations. One of the key steps in this process is the development of comprehensive security policies. These policies should include robust data protection standards and role-based access controls that govern how third-party vendors interact with the company’s systems and sensitive data. Such policies need to be regularly updated to keep pace with the ever-evolving threat landscape.
Another crucial component is the continuous monitoring of security across the entire supply chain. Deploying SIEM systems allows organizations to detect and respond to cyber threats in real-time, offering a more dynamic and immediate defence. Similarly, MDR tools provide enhanced monitoring capabilities that help identify and neutralize potential threats before they cause significant harm.
In addition to these measures, the use of threat intelligence is essential in staying ahead of emerging risks. By leveraging threat intelligence, companies can remain informed about the latest cybersecurity threats and trends. This proactive approach enables organizations to take pre-emptive action, safeguarding critical assets and ensuring that they remain resilient against future attacks.
In conclusion
To sum up, the energy and utilities sectors face unprecedented cybersecurity challenges, but by adopting a comprehensive approach they can mitigate risks and stay ahead of evolving threats. From securing OT environments to addressing IoT vulnerabilities and mitigating supply chain risks, a robust cybersecurity strategy is critical to maintaining operational resilience and protecting vital infrastructure.
➡️Would you like to learn more? Write to marketing@hwgsababa.com.
#WeMakeYouCyberSafe
[2] 2024 X-Force Threat Intelligence Index, IBM
[3] 2024 X-Force Threat Intelligence Index, IBM
[4] The 2024 Benchmark Report on IoT Security, Palo Alto Networks