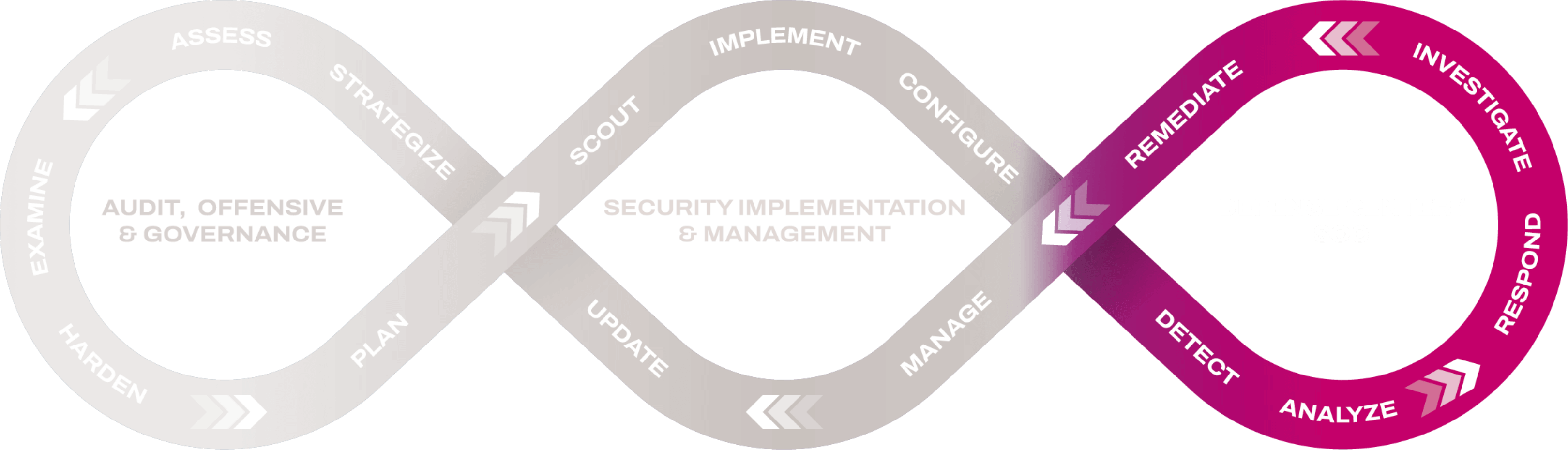
We understand the challenges of maintaining observability through real-time processes to manage threat exposure and ensure resilience across complex ecosystems. By transforming your security operation model and taking over the critical resource – and expertise – consuming aspects, we empower your organization to navigate the evolving threat landscape effectively. Our full-scale 3-level SOC provides round-the-clock monitoring, incident detection and response, and comprehensive intelligence and threat hunting, guaranteeing the security of your critical systems even against complex cyber threats.
With a team of 70+ certified cybersecurity experts, we surpass traditional security measures by offering continuous monitoring and management of your IT, OT, and IoT environments. Our SOC experts diligently observe your security logs and analyze processes for anomalies, enabling the identification of patterns even in complex cybersecurity threats that may disguise themselves as legitimate processes. By analyzing data from multiple sources across your network and mapping them to attackers’ tactics, techniques, and procedures (TTPs), we can proactively identify and address security breach attempts before they harm your systems.
Solutions
Enhance your security operations with effective incident detection, investigation, and response, continuous visibility into your infrastructure, applications, and data.
SOC case studies
Check security solutions for
Do you want to learn more
or schedule a call for expert consultancy?
Fill out the form below.