A Penetration Test on a PLC highlights how protecting an ICS environment is not trivial, as these systems weren’t designed to resist cyber attacks.
This means that you have to somehow integrate cybersecurity resilience measures inside and around the ICS. Such measures include, for example:
- perimeter protection, such as firewalls to reduce the risk of unwanted network traffic;
- network monitoring– preferably non-intrusive, ICS-specific, anomaly-based monitoring so as not to create any additional load on ICS networks;
- endpoint protection and monitoring to reduce the exposure of PLCs to attacks via remote connections.
A Penetration Test on a PLC Reveals Hidden Vulnerabilities in ICS
Another very important aspect is to identify and understand the risks. What are the attack surfaces, methods implemented, vulnerabilities and potential consequences? Moreover, it is fundamental to continuously assess and evaluate the probability of potential attacks.
One method of obtaining detailed information on risk exposure is penetration testing, the goal of which is to identify attack vectors and simulate an actual, controlled, and aware attack on the system. However, carrying out a penetration test in an ICS environment requires a significantly different careful approach than a standard penetration test activity for IT systems. ICS systems contain sensitive equipment – such as PLCs – equipped with a similarly sensitive processing unit, which can cause freezes, configuration resets, and failures if overstressed due to low stack management.
Standard penetration tests such as a simple port scan performed by tools like Nmap may be enough to overload the processing unit. Due to weak network stack management, some devices cannot handle the number of network packets generated by Nmap and similar tools. Therefore, it is best not to perform penetration tests in a live ICS environment, but to carry them out only in a controlled test lab environment or during scheduled downtime.
Integrating a Penetration Test on a PLC into Your ICS Security Strategy
There are many penetration testing methodologies to choose from, though few are tailored to ICS. One methodology compatible with ICS is the “zero entry”, which is composed of four phases: reconnaissance, scanning, exploitation and post-exploitation.
Reconnaissance focuses on collecting information about the target, such as IP address and Domain Name System (DNS) records, and reading common vulnerabilities for the target PLCs. Scanning consists of actively scanning the target for open ports, detecting the operating system, and running services.
Nmap, including Nmap Script Engine (NSE), is an example of a tool that is often used for scanning. In the event that a vulnerability is detected, the attack phase moves to exploitation. In most cases, such vulnerabilities are used to gain access to the system through different services running on the PLC. After exploiting the vulnerability, it is preferable to make the access persistent. However, not all services provide the opportunity to create a persistent backdoor.
Post-exploitation could involve maintaining access to the system, which is what an APT does when it establishes a path to communicate with the command and control center, which is used to send intelligence information about the target system and to upload new exploits/malware. Trail obfuscation to hide the attack represents the fifth step.
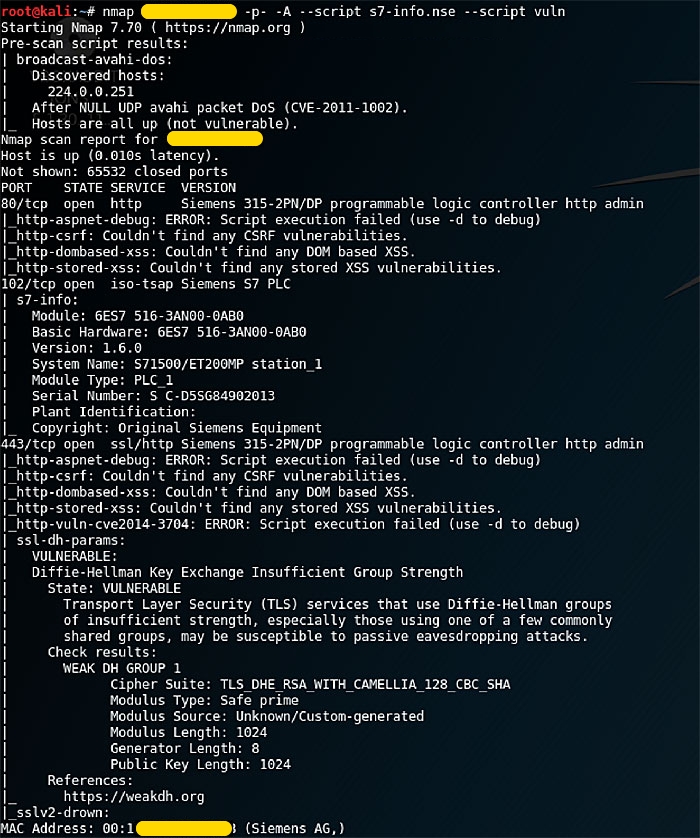
For many PLCs, details about the system can be extracted leveraging from a controlled Nmap scan. However, this should be done carefully to avoid disrupting its operation.
In one of the penetration tests, Nmap scanning – using scripts in Nmap Script Engine (NSE) – revealed MAC address, hardware and firmware information, open ports 80, 102, and 443, and more. This detailed information can be used to develop exploits and investigate vulnerabilities to specific PLC series.
Many of these vulnerabilities are reported and discussed in the National Vulnerability Database. By exploiting them, in many cases it is possible to crack the password, gain access to the PLC… and shut it down.
Discover how HWG Sababa protects ICS environment with its dedicated OT business unit!
Important Note
The purpose of this article is educational and informational. Any unauthorized action toward any control system on a public or private network is illegal. The information contained in this article is intended to make people understand how necessary it is to improve defense systems, and not to provide tools to carry out the attack. Breaking into a computer system is punishable under criminal law and can cause serious damage to property and people, particularly when it comes to ICS. All the tests that are illustrated were carried out in isolated, secure, or manufacturer-authorized laboratories.